I asked a hacker to spy on me via my Amazon account. It took him 5 minutes to break in

A few weeks ago, I received an email. It looked like it came from Amazon – and it was advertising ridiculously great deals on recording equipment.
I clicked on it, and entered my Amazon login and password.
That email gave hackers access to my home.
This was a fake phishing attempt. I knew it was coming.
Still, Jack Koziol, a hacker who started a security firm called Infosec, said that 80% of people who get hacked are lured in by phishing attempts sent through email or social media.
It's an old school technique, but the perps keep getting better at it.
Koziol and his team are "white hat hackers." They hack into systems to discover their vulnerabilities and then give that information to companies so they can patch up the leaks.
My goal was to see what hackers could do to my smart home if they managed to get into my Amazon account.
Sponsored
Inside Joshua's home
The next morning, my family was going through our normal morning routine.
The theme to Twin Peaks was playing in the bathroom, indicating it’s my son’s turn to shower.
Then, suddenly, the music switched to the living room, where my daughter and I were hanging out.
And the music changed — to Motörhead's "Ace of Spades".
Sponsored
Back at hacker headquarters . . .
At the Infosec office in Chicago, an employee named Cameron Bulanda was having a lot of fun.
“Right now, we’re taking a look at all their devices,” Bulanda said. “We’ll start by turning off the couch light that they have there.”
Back in Seattle, the lights blinked on and off.
Later, Koziol gave me a description of each step that Bulanda took.
Sponsored
Using just the Alexa app, Bulanda made a complete list of all my smart home devices and their addresses on the web.
“So now he’s got his lay of the land,” Koziol said. “It’s much like a criminal broke into your house — they’re going to look around, see what’s in there, see what’s valuable.”
Bulanda changed the music to Thriller — and then spied on me through the Echo’s camera to see how I liked it.
Bulanda then moved on to my contacts. “I actually inputted myself in there as a malicious hacker,” he said, “and gave myself drop in privileges, so if I wanted to go in there from a different phone, I could do that.”
Sponsored
Koziol told me this is one of the first things hackers do. They put in a back door, so if they get kicked out, they can get back in.
Bulanda noted my reminders and alarms, as well as my shopping lists.
“We could always set a routine," Bulanda said. "Maybe if we wanted to wake him up in the middle of the night. Or turn on all his lights when he’s gone to cause a higher electric bill.”
“It’s scary how easy this is,” said Koziol.
Back in my home, my daughter and I were amused by the whole experience. It felt like being in the world’s lamest haunted house.
Sponsored
But Koziol said I should take it more seriously.
“If I’m targeting you,” he said, “and I have some specific goals — let’s say I want to steal your bank account information, or I want to gather information to discredit you in public — there’s probably a lot of information in there that’s going to help me.”
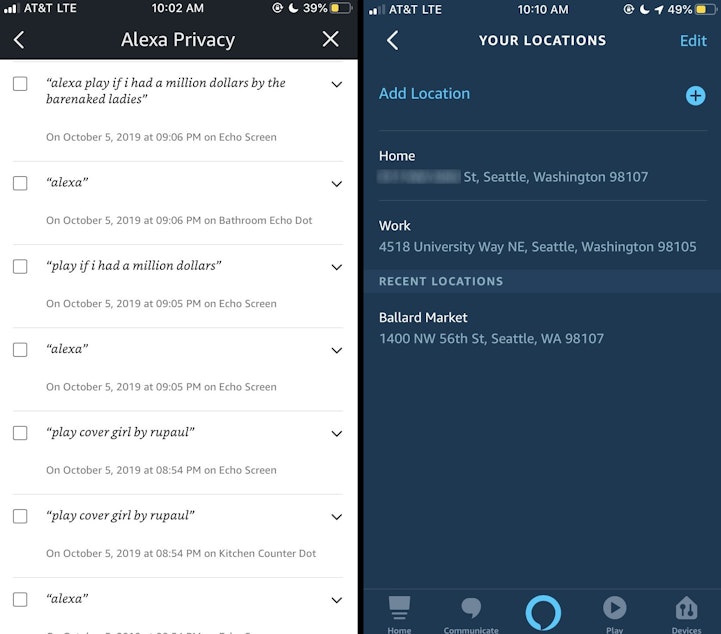
Koziol said most hacks start with a theft of credentials, like with the email that got me.
It’s difficult to hack into Alexa’s hardware — in fact, white and black hat hackers all over the world are still working on it. They're tearing Echos apart, probing for weak spots and posting their findings online.
Others are experimenting with malicious skills that can hide an eavesdropping program inside an Alexa calculator skill. Amazon programmers typically remove those vulnerabilities before they reach the public.
Amazon's head of digital security, Damian Hasse, said Amazon has built one of the best defenses in the industry against hackers. "It has multiple layers," he said. "So if you peel one layer of security, boom. There is another one there.”
You can hear more about those defenses, and how hackers are trying to breach them, in the full podcast episode of Primed.
But there's still a major vulnerability in Amazon's defenses: Us.
When it comes to our smart homes being hacked, we don’t need to worry as much about someone smashing a window.
Instead, we have to be careful we’re not the one handing them the key.
Music on this episode of the Primed podcast includes Ripples on an Evaporated Lake by Raymond Scott.




